
- Home
- Managed Services
- Cyber Security
- Blog
- About Us

We 365 Admin Support, just simplify your IT problems
Call for a free support. +91 96666 59505Platform Partnership
- Who We Help
- Shop
- Contact
- News





A new variant of the MacSync information stealer is posing a threat to macOS users, delivered via a digitally signed and notarized Swift application.
According to security experts at Jamf, an Apple device management platform, this method marks a notable advancement from older techniques that relied on less complex “drag-to-Terminal” or ClickFix approaches.
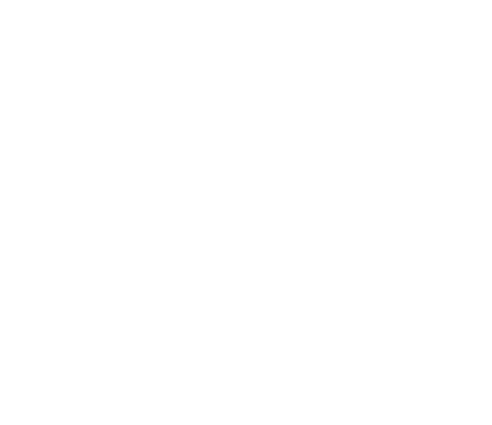
“It’s distributed as a code-signed and notarized Swift application packaged within a disk image named zk-call-messenger-installer-3.9.2-lts.dmg, available at https://zkcall.net/download, effectively eliminating the need for any terminal interaction,” the researchers outlined in their recent report.

During their analysis, Jamf noted that this new variant of MacSync possesses a valid signature, allowing it to bypass macOS’s Gatekeeper security checks.
“Upon examining the Mach-O binary, identified as a universal build, we verified that it is both code-signed and notarized. The signature corresponds to the Developer Team ID GNJLS3UYZ4,” Jamf reports.
However, following a direct notification of the certificate to Apple, the signature has subsequently been revoked.
This malware is installed on the system via a dropper in an encoded format. After decoding the payload, researchers uncovered the typical characteristics associated with the MacSync Stealer.
The researchers observed that the stealer incorporates a series of evasion techniques, such as inflating the DMG file size to 25.5MB by embedding fake PDF files, removing scripts from the execution flow, and conducting internet connectivity checks prior to execution to avoid detection in sandbox environments.
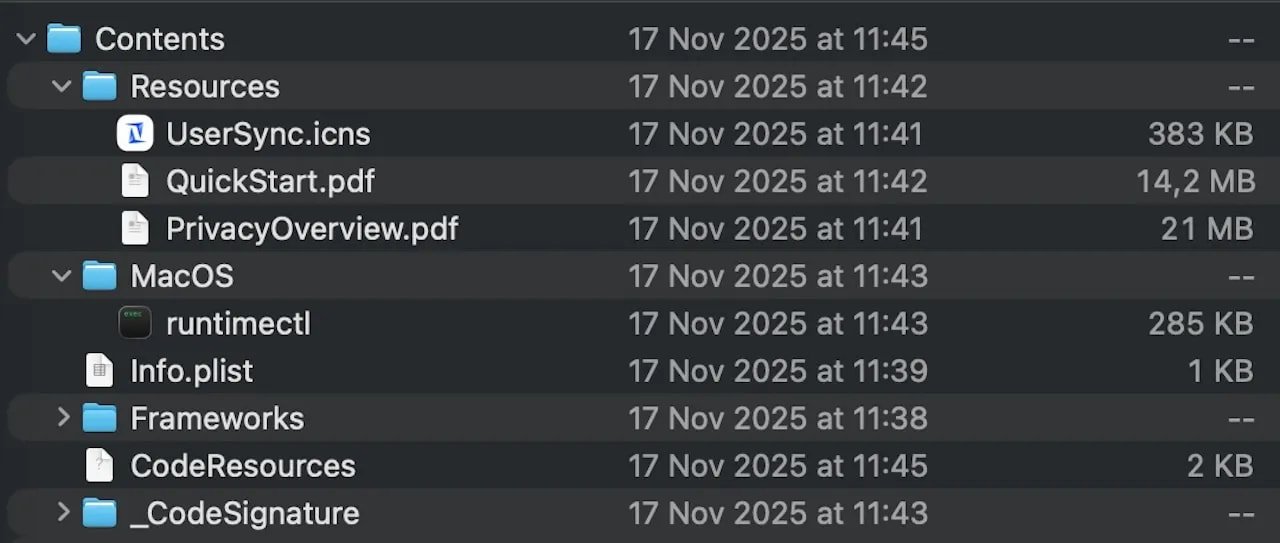
The stealer first appeared in April 2025 under the name Mac.C, attributed to a threat actor known as ‘Mentalpositive’. It gained significant traction by July, finding its place in the lucrative market of macOS stealers alongside AMOS and Odyssey.
A previous evaluation of Mac.C by MacPaw Moonlock showed its capability to steal iCloud keychain credentials, passwords from web browsers, system metadata, cryptocurrency wallet details, and files from the local filesystem.
Interestingly, in an interview conducted with Mentalpositive by researcher g0njxa in September, the malware creator mentioned that the tightening of app notarization policies in macOS 10.14.5 and later had a significant impact on their development strategy, as reflected in the most recently detected versions.